How to recognize and avoid password phishing?
“Wait… Did someone really just log into my account? Do I really need to change this password? Did I even do something on this account recently?”
This is the monologue that should occur every time a password phishing email appears in the inbox.
And yet, in 2020, this monologue failed to happen in 74% of U.S. companies. That is the percentage of successful phishing attacks for last year.
What is password phishing?
Password phishing is a scam that is carried out through common lines of communication: email, instant messages, text message and even phone or video calls.
The most common practice is email-based scamming. The purpose of it is to trick the recipient into giving away sensitive information.
The information sough after usually includes:
- passwords;
- date of birth;
- credit card number;
- social security numbers;
- home address.
Commonly, the recipient receives a professional and official looking email from a seemingly trusted source (e.g. bank, place of education, social media sites and other services that a person might use). The email is designed to look like a credible one, so the victim often falls for the trick and follows the given instructions.
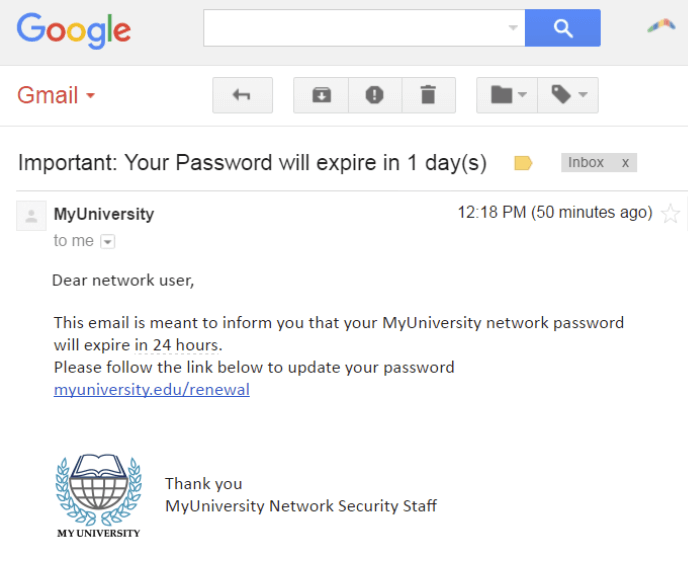
For instance, the email might ask you to urgently change your password or provide other sensitive information by clicking the link. Common reasoning provided by the perpetrators is that your credentials have supposedly been breached; or you are being contacted by government authorities; or your bank has stopped a fraud related to you.
However, all the data you provide is sent to the criminals, instead of the organization you thought to be in contact with.
Why is phishing the most popular cybercrime?
According to Statista, phishing was the most popular cybercrime in 2020. Notably, the spike in password phishing crimes can be linked to the Covid-19.
FBI reported that there were 11 times more phishing complaints in 2020 compared to 2016. The reason behind this is logical. More people are working from home – a less secure environment – and thus there are naturally more victims to target.
The second alarming reason behind the popularity of password phishing is the improvement of artificial intelligence and the growth of spear phishing methods. Spear phishing works similarly to regular phishing, but each email is custom designed for each recipient. The reason behind this is spear phishing often targets specific, high-profile people in companies, usually C-level executives or department directors.
For instance, if a general phishing email can ask you to log in to a form that looks like a common website, a spear-phishing email might include your name or even more of your personal data. This significantly increases the chance you will trust the recipient more and provide your data.
The 2020 Verizon report suggests that 86% of all breaches were financially motivated. Your data is a commodity and malicious parties will go far in order to get it.
Let’s learn how to protect it.
How to recognize a phishing email?
When you know precisely what the red flags are, it becomes incomparably more difficult for a criminal to trick you.
This is a checklist that you should always run through whenever a you get a suspicious email (asking for your personal information, is filled to the brim with links, offers something that sounds too good to be true, etc.).
Sender
Always check who you’ve received an email from.
If your bank sends you an email using a Gmail, Hotmail, Yahoo mail or a similar popularsuffix, you can be sure that this email was not sent by your bank.
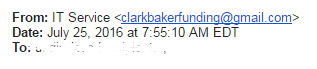
Also, carefully investigate the domain that follows “@” in the sender’s address. If it seems that you’ve received a letter from Facebook, but it was sent from john@ Faceboook.com(three Os), that’s a huge red flag.
(Facebook provides a list of email addresses that they send their official emails from. If the one you received is not on this list, Facebook is not the sender.) Apply this rule to all emails that you get from organizations – if something seems suspicious, contact a representative from the organization and ask to provide an official list of their email addresses.
Links
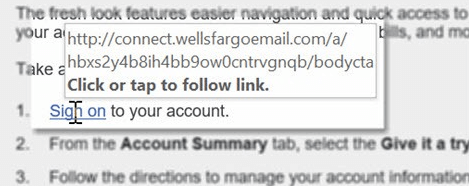
If the email contains a link that looks trustworthy, instead of pressing on it hover on it with your mouse. At the bottom of the window (or next to the link), you should see the domain you will be directed to. If that is not a domain your expected, never click on it.
Domains
If you did (accidentally) click on a suspicious link, be very cautious on the website you’ve been directed to. Be especially careful if it asks you to fill in any personal data. In popular password phishing practices, it is common to replicate the website (f.e. Facebook or Gmail login field) on a similar domain but change only a letter or add a word to it.
For instance, instead of the wellsfargo.com domain, you might see a wellsfargoofficial.com or wwellsfargo.com– a minor change that might be easy to spot, but once you do you can instantly reveal it’s a scam.
Password manager can protect you from password phishing.
Password manager provides you an additional level of security. This might help you protect yourself from an expensive and dangerous password phishing attack.
For example, PassCamp password manager provides you with an autofill feature. This feature automatically detects websites you have saved passwords for. For example, if you click on a suspicious link, it will likely direct you to a non-original website. The password manager will then show you that you don’t have any passwords saved on this domain. This provides you with an easy way to notice spoofs in fake URLs.
In addition to that, PassCamp supports and encourages high password hygiene standards. With PassCamp, you always have strong and complex passwords, additionally protected with Two-factor Authentication.
Lastly, there’s a simple rule regarding password phishing emails – never trust any email that comes to your inbox.

Always be skeptical and vigilant.
Ask yourself, is there really is a basis for this email, and run the email through the checklist.
Be cautious and stay safe!




